I built and blogged about building my own DIY NAS back in 2012 and I’ve been repeating building a new DIY NAS once or twice a year ever since. One of the most frequently asked questions across those blogs has been, “How do you access your DIY NAS from the Internet, Brian?”
My answer to that question has always been “I don’t.” For the most time I’ve had a DIY NAS, I just didn’t have much need or interest in accessing the contents of my NAS from outside my home. At first, I only used my DIY NAS for backing up the computers that I had at home. But slowly over time, I’ve transitioned to using my DIY NAS as my primary storage for all of my data.
 Consequently, accessing my data remotely has been more and more important over the years. Primarily, I’ve used services like Google Drive or Dropbox to access critical data and synchronize changes made to it across all my machines. For quite a while this has been both easy and cheap. But I started creating more content, especially videos for my YouTube channel, and this solution slowly began to break down and become more expensive.
Consequently, accessing my data remotely has been more and more important over the years. Primarily, I’ve used services like Google Drive or Dropbox to access critical data and synchronize changes made to it across all my machines. For quite a while this has been both easy and cheap. But I started creating more content, especially videos for my YouTube channel, and this solution slowly began to break down and become more expensive.
Over the past two years, I’ve made a few halfhearted attempts to install and configure a VPN endpoint within, or at the edge of, my own network. Every time that I tried, I ran into issues–mostly all related to my lack of expertise–and set it aside to figure out another day.
For a while now, a few people have been encouraging me to check out Tailscale. In fact, Pat’s been telling me routinely about how he’s made his life easier with Tailscale and insisting that it was really simple to set up. While I have had no reason to doubt Pat’s assessment, I’ve also learned that there’s a cornucopia of topics that Pat thinks are painfully simple which completely short-circuit my brain.
What is Tailscale?
Over on Tailscale’s website they describe Tailscale as “A secure network that just works. Zero config VPN. Installs on any device in minutes, manages firewall rules for you, and works from anywhere.”
You create an account with Tailscale, you install a client on each machine, associate those clients with your account, and Tailscale encrypts traffic between any of your endpoints.
Tailscale was as easy as Pat made it sound every time he told me about it. In fact, I think it was easier!
How am I using Tailscale?
Out of curiosity, I set up Tailscale on a few different devices and without any effort I had Tailscale up and running on my phone, my tablet(s), two different Raspberry Pis, my laptop, my desktop computer, and on my OpenWRT router.
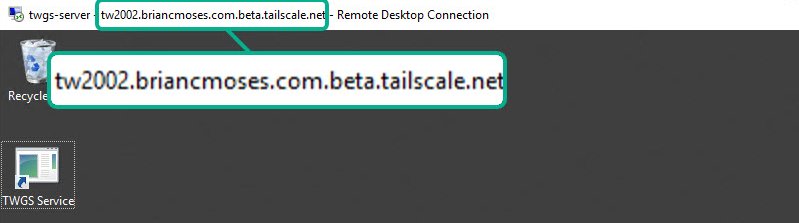
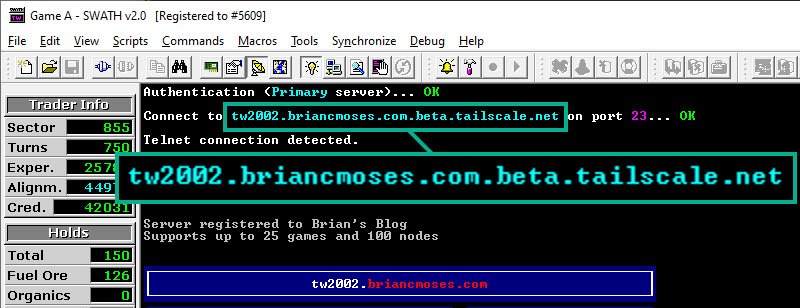
Remote Desktop access to my Tradewars 2002 game server
A couple years ago, I wrote a nostalgic blog about Tradewars 2002 which convinced me to spin up my own Tradewars game server on a small virtual machine hosted in Azure. For a long time, I’ve lived with exposing more than just the Tradewars game server’s port in order to remotely access the machine.
Implementing Tailscale on the game server let me close down the port(s) that I had exposed–and probably never should have–on the TW2002 virtual machine.
This is something that I could’ve accomplished in the Azure portal on my own by setting up some firewall rules in Azure and also on the virtual machine. But it was so much easier to just completely close it down and use Tailscale instead.
As an added benefit, my super-secret outer space trading strategy is now happening over an encrypted tunnel!
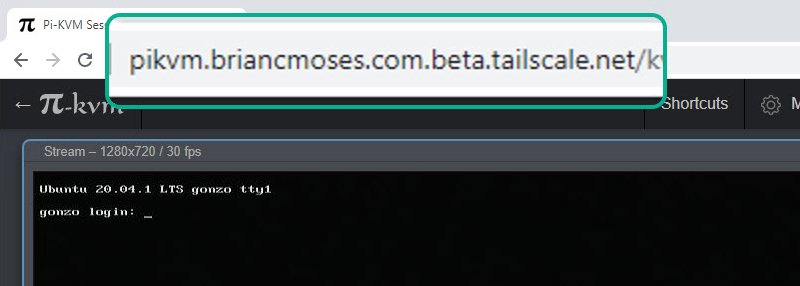
Pi-KVM
If you’ve read my two-part series of blogs about Pi-KVM then you’re already aware that Pi-KVM is an awesome little project that allows you to build an inexpensive KVM-over-IP using a Raspberry Pi 4 Model B (2gb version), a video-capture device, and an assortment of USB cables.
- Part One: Pi-KVM: an inexpensive KVM over IP
- Part Two: Pi-KVM: Controlling a 4-port KVM and setting up Tailscale
Combining the Pi-KVM and Tailscale is a really compelling pairing which demonstrates the value of both products. If I had a friend who was having a computer problem in another location (near or far), I could give them the Pi-KVM, they could hook it to their computer and network, and thanks to Tailscale I could access the Pi-KVM interface remotely. I could access the machine’s BIOS, boot from an ISO, or remotely access the native operating system without much effort at all.
A shotgun approach to access the contents of my DIY NAS remotely
Tailscale’s recommended approach is to put the Tailscale client on all of the devices and assemble a mesh network of connected endpoints. This assumes that you’re able to install the client directly on each machine. Unfortunately, FreeNAS (or TrueNAS) does not include the Tailscale client in their base operating system and they don’t really want you tinkering with the operating system at all, so the Tailscale-recommended approach is not as straightforward.
In evaluating my options, I knew I’d need to use Tailscale’s relay node if I wanted to be able to access my NAS using Tailscale. It seemed like I had a few options using Tailscale as a relay node:
- A jail hosted on my FreeNAS server.
- A virtual machine on my homelab server.
- On my OpenWRT router.
For the time being, I have opted for the third option. I knew that running it on my own OpenWRT router was possible thanks to Pat’s blog about putting Tailscale on his Mango OpenWRT router.
I configured the relay node to relay for the subnet that my NAS (and the rest of my home network) is on. I wound up deciding that if I was going to compromise by moving away from Tailscale’s mesh of encrypted network endpoints, then I would do so in a way that provided the maximum of possible utility. In this way, I was using Tailscale pretty similarly to a traditional VPN–everything on my network at home is accessible from outside of my network–provided the computer I’m using it from (my laptop) is running a Tailscale client too.
So what do I think?
Ultimately, I would’ve preferred adhering to the full-Tailscale method and installing client(s) on every machine that I want to be reachable from my other machines running Tailscale. My lack of understanding of FreeBSD and how FreeNAS is architected were significant enough of obstacles that I made a compromise.
I expect that it is possible that a FreeNAS enthusiast could create a jail, install the FreeBSD Tailscale package in the jail, and tighten the scope of the Tailscale relay node down to only the IP of the NAS. Perhaps this will be a topic of a future blog? Or even better–maybe somebody will answer this question in the comments below?!
Regardless of my obstacles with FreeNAS, Pat absolutely was correct–Tailscale makes all of this so much easier! I’ve installed Tailscale on devices with very different hardware, running a number of different operating systems, and numerous different use cases. All of it was really straightforward and easy to set up. I didn’t have to create any firewall rules–it all just worked.
I’m excited about the possibilities that Tailscale presents. They recently added endpoint sharing as a Public Beta, which is a really useful concept that I’m going to be exploring as part of future blogs. So please stay tuned!